The Repository
When democracies allow their intelligence services to conduct large-scale electronic surveillance of communications data, they must do so within the limits of the law. They must also ensure that this practice is subject to effective and independent oversight. Yet, what does that mean in practice, and how can one best distinguish between good and poor legal safeguards, as well as between efficient and inefficient oversight dynamics?
This website compiles good practices on the bulk surveillance of (foreign) communications from different national intelligence laws and oversight systems across Europe, North America, and Australasia. It is by no means meant to be exhaustive, and we invite your comments and additional suggestions. If a particular example is taken from one country, this does not exclude the possibility that the same – or similar – rule or practice exists in another jurisdiction.
Our Research
To find international good practices, we studied a wide range of different public resources, such as commentary on intelligence laws, oversight body reports, strategic litigation materials, as well as commentary on intelligence policy. We developed our own analysis scheme (see Intelligence Oversight Analysis Cycle) and conducted a series of interviews with a range of different experts (legal scholars, computer scientists, public servants and oversight professionals, industry representatives, etc.) to obtain further information on current practices. Once we had collected enough information, we initially wrote a draft compendium and organized two expert workshops – one with oversight body representatives in May 2018, and one with European and North American civil society experts in June 2018 – to further test and refine our findings. Since then, we have been continually updating our pool of good-practice examples with the help of the European Intelligence Oversight Network and other research projects. If you know of additional examples that should be included in this collection, we would love to hear from you.
What is a good practice
We consider a practice to be good when, by comparison, it provides an improved safeguard against potential violations of rights, or because it stands out in the way that it solves a common governance challenge, or because it may make innovative use of technology for the benefit of greater oversight effectiveness.
Although our method may allow us to identify international high-water marks regarding the governance and control of the bulk surveillance of communications, we do not hold enough information to rate the overall quality of individual surveillance laws or national oversight frameworks. Too many individual factors contribute to this, and we cannot reflect on all of them here. Moreover, there are limits to what a comparative study of this kind may reveal. Every country has its unique social, legal, and political setup that influences the governance and reform of intelligence. As we do not account for these differences here, we cannot credibly make declarations on the overall governance framework in which these good practices are embedded. This also means that the amount of citations that a national law or oversight regime receives in this compendium cannot be construed as a suitable indicator for the overall quality of the bulk surveillance regime in each country.
Focus: Signals Intelligence
Our focal points are the legal frameworks and oversight regimes regarding non-targeted signals intelligence (SIGINT), with a special emphasis on foreign communications data. This provides intelligence services “mass access […] to data from a population not itself suspected of threat-related activity.” Unsurprisingly, non-targeted (or “bulk”) SIGINT capabilities are often considered to be the crown jewels of a national intelligence community. It is a technically sophisticated and highly complex intelligence-gathering discipline that involves significant levels of international cooperation and was developed covertly over time by many democracies. The National Security Agency (NSA) of the United States famously proclaimed that, due to the shift toward digitized means of communication, we were now living in “the golden age of SIGINT.” This said, the bulk surveillance of foreign communications is but one practice in a much larger universe of intelligence-gathering disciplines. Targeted surveillance and active computer network operations (i.e., getting access to datasets via hacking computer networks, etc.) are two other prominent examples. They are, of course, also very important, and they, too, must be subject to rigorous oversight. Bulk collection is usually conducted by intercepting large amounts of data from fiber optic cables as well as radio and satellite links, but data can also be collected in bulk through hacking operations, which can be more effective accessing data in a non-encrypted form, as opposed to data from transit links, which is usually encrypted nowadays.
Due to our own resources, and for the sake of reducing complexity, we decided to focus only on bulk collection of (foreign) communications on this website.
Intelligence Oversight Analysis Cycle
What are the relevant aspects that one needs to consider when it comes to creating a legal basis for – and the democratic control of – bulk surveillance? According to what standards and criteria can we assess the quality of either a legal provision or an oversight practice? Clearly, this, too, needs further unpacking. We break down the most relevant governance aspects for the bulk surveillance of foreign communications into eight phases.
Whether it is the initial strategic planning, the application processes, or the authorization/approval processes that are required prior to the execution of bulk powers, one can depict in legislation and actual oversight practices a range of relevant standards that democracies ought to meet. The same holds true, of course, for the implementation of bulk powers in practice: This, too, involves many processes and constitutional obligations that become more readily apparent when the entire cycle is depicted in its different stages. Our multi-stage model is based, in essence, on the more common intelligence cycle that has traditionally been used to explain the different stages required to produce actionable intelligence.
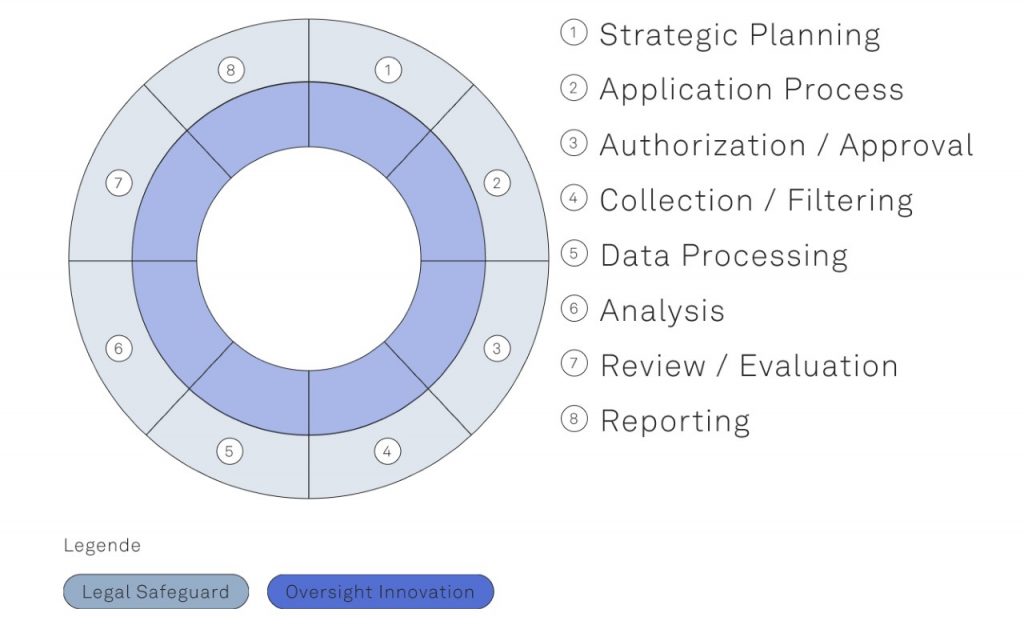
Legal Safeguards and Oversight Practice
We decided to include both legal safeguards and oversight practices for every oversight phase, because they are each extremely important and mutually constitutive. Comprehensive intelligence legislation is a necessary but not sufficient condition for the effective democratic control of bulk surveillance. Not everything can be legislated: For example, for reasons of source protection, national intelligence laws may not provide detailed accounts of individual tools that are to be used in the field. Yet, case law – for example, on the quality of law or the strict necessity test developed by the European Court of Human Rights – provides some orientation on standards that modern intelligence laws ought to meet. Whether or not these standards are then observed in actual practice is another story. This needs to be independently and effectively reviewed. What matters here are the actual dynamics of judicial oversight as well as its resources, legal mandate, and technological tools.
Caveats
- “Borrowing” from other surveillance practices
There are many fine distinctions between targeted and non-targeted surveillance practices and the protections that are given to national and non-national data in national intelligence laws. When we run the risk of comparing things that are fundamentally different, we account for those important differences and make a case for why, as an exception, we are still drawing on a targeted surveillance regime in order to bring attention to an existing practice that, we think, should be given further consideration in bulk regimes. For example, it makes good sense to borrow from regimes on “targeted surveillance,” such as the US Section 702 program, which is meant to target only the internet and telephone communications of people outside the United States to gather foreign intelligence information. We believe that some safeguards or oversight practices that currently apply only to targeted regimes are equally suitable for bulk collection because they, too, involve big data challenges. When we borrow from targeted collection programs, we make this explicit with the help of an exclamation mark.
- Triangulation
Second, although helpful in identifying and discussing key governance challenges, our multi-stage model, we acknowledge, is too linear, in the sense that an intelligence service often combines the data collected from different gathering techniques. For example, intercepted bulk data may trigger further bulk equipment interferences, and data from bulk equipment interference may be fused with other datasets collected from communications providers. Our model does not look into the triangulation of different digital powers of modern intelligence services.